DDoS Attack with 1.5 Billion Packets per Second: A Warning Sign for IoT Security

In the second week of September 2025, security researchers recorded one of the largest known Distributed Denial of Service (DDoS) attacks. The target was an undisclosed DDoS protection provider in Western Europe. The attack peaked at around 1.5 billion packets per second. Such values are considered extreme and highlight how the threat landscape is worsening due to the abuse of Internet of Things (IoT) devices.
According to FastNetMon, which documented the attack, the systems of the provider were targeted on September 8. Within a very short time, massive amounts of small packets hit the infrastructure. The goal of such attacks is to overload routers, firewalls, or defense systems by forcing them to process more packets than technically possible. Unlike classic attacks that mainly clog bandwidth, these “packet floods” specifically aim to overwhelm the processing power of network equipment.
Remarkably, the source of the attack was highly distributed: data streams came from more than 11,000 autonomous networks worldwide. Behind these packets were tens of thousands of compromised devices – mainly CPEs (Customer Premises Equipment) such as routers and small servers, but also many IoT devices. These had been hijacked beforehand and linked together in a botnet.
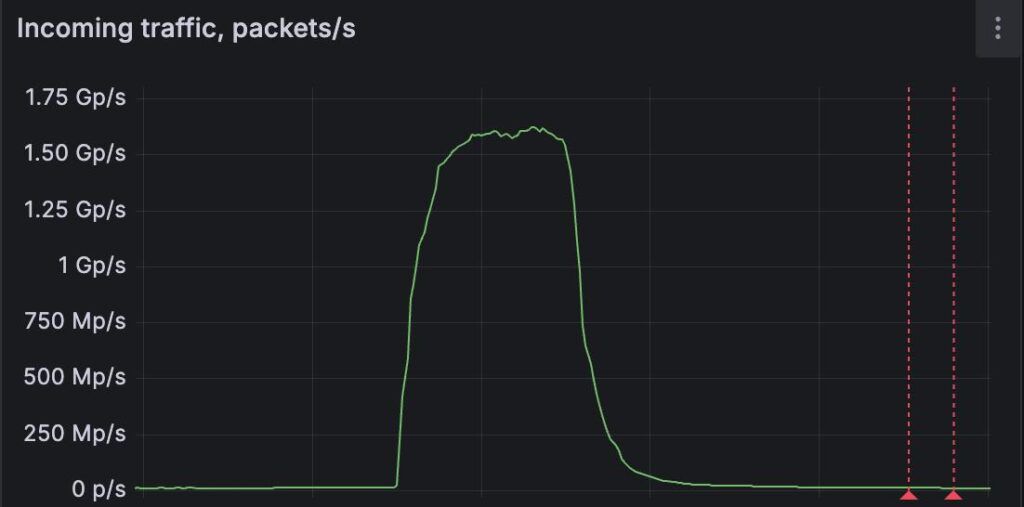
Visualization of the DDoS attack on September 8, 2025. Screenshot: FastNetMon
Why IoT devices are a problem
The case illustrates that not only servers or PCs play a role in cyberattacks. Millions of everyday devices – from internet routers to connected surveillance cameras – are online. Many of these devices are poorly secured: factory settings remain unchanged, security updates are missing, default passwords are left active. Once attackers hijack a device, they can secretly use it for their own purposes.
A DDoS attack then works like a “storm of raindrops”: a single drop is harmless, but billions at once can flood rivers. Similarly, a flood of small packets, coordinated from thousands of devices, can overwhelm networks.
Defense measures in this case
In this attack, the provider’s defense system responded immediately. Using telemetry data, the attack was detected and scrubbed. Additionally, so-called Access Control Lists (ACLs) on routers blocked certain protocols used for amplification. Still, FastNetMon called for ISPs to take stronger action. Specifically, they should stop malicious traffic at the edge of their networks instead of passing the load downstream. “This event is part of a dangerous trend,” said Pavel Odintsov, Founder of FastNetMon. “When tens of thousands of CPE devices can be hijacked and used in coordinated packet floods of this magnitude, the risks for network operators grow exponentially. The industry must act to implement detection logic at the ISP level to stop outgoing attacks before they scale.”
International context
The attack ranks among the largest ever recorded by packet rate, though it did not set the absolute record. Cloudflare reported in April record-breaking attacks of up to 5.1 billion packets per second and more than 11 terabits per second in bandwidth. What is clear: the number of extremely large-scale attacks has risen sharply since 2024. In the second quarter of 2025 alone, Cloudflare counted over 6,500 such incidents.
The threat is growing. Even specialized defense companies can only prevent service outages with high-performance systems and worldwide filtering. For ordinary companies or private individuals, an attack of this scale would be impossible to withstand.
Implications for IoT security
The case shows that the real vulnerability is not only at the target side, but mainly in the devices being abused. Every unsecured webcam, every poorly configured router can become part of a global attack. For device owners, the consequences are often invisible – their device keeps working while secretly serving other purposes. In the end, however, society bears the costs: higher security expenses, unstable networks, and service interruptions.
It is becoming clear that binding minimum standards for IoT devices are needed. Secure defaults, regular updates, and blocked remote access could prevent devices from being hijacked en masse. ISPs are also called upon to detect and block suspicious traffic early. Without such measures, the internet risks being further destabilized by botnets made up of insecure everyday devices.
Conclusion
The attack with 1.5 billion packets per second is a wake-up call. It proves that unsecured IoT and network devices have long become a serious threat to internet stability. As long as manufacturers allow weak standards and ISPs fail to consistently stop malicious traffic, such attacks will continue to increase.
Summary (tl;dr)
- Attack on DDoS protection provider in Western Europe with up to 1.5 billion packets per second.
- Source: compromised routers and IoT devices from over 11,000 networks worldwide.
- Defense by scrubbing systems and router filters successful.
- Comparable records: Cloudflare recently reported up to 5.1 billion packets per second.
- Main issue: Insecure IoT devices, missing standards, and insufficient ISP filtering.














