DNS rebinding: IoT devices are wide open for attacks
A team of experts from Armis IoT-Security recently published a study on the status quo of the security of IoT devices in companies.
According to the study, at least half a billion devices on the Internet of Things are not protected against DNS rebinding attacks.
What is DNS rebinding?
In the WWW, the Domain Name System (DNS) is used for name resolution. For example, if a user enters a web address in his browser, this request is forwarded to his provider’s DNS server. There the correct IP address is automatically determined for the queried domain – and the browser request is then forwarded to the correct server.
DNS rebinding uses an almost decade-old bug in web browsers that allows an attacker to bypass a victim’s network firewall and use his web browser as a proxy to communicate directly with vulnerable devices on the local network.
In a DNS rebinding attack, the attackers use their own DNS server along with a manipulated website that has been prepared with a Javascript. The target is first lured to this website (for example via spam emails or harmless links on other sites; paid advertising), but the IP address used is marked as only valid for a short time.
On the next request from the victim, the DNS server then replaces the IP address with an address from the local network. Now the Javascript uses the new IP address. In this way, for example, the attacker can creep into a company network.
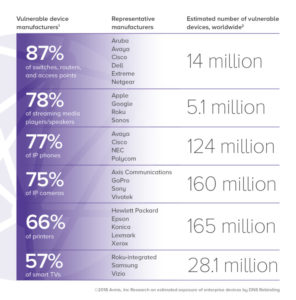
Armis explains that these attacks can also be carried out against numerous IoT devices and other network-capable products. About 77 percent of the IP telephones used worldwide are not sufficiently protected against DNS rebinding.
Routers, switches and access points at risk
In IP cameras, 75 percent are said to be vulnerable. For networked printers 66 percent, for smart TVs 57 percent, for media players 78 percent and for switches, routers and WLAN APs as much as 87 percent.
According to Armis, devices of many well-known brands are not or only inadequately protected against DNS rebinding attacks. These include devices from network manufacturers Aruba, Avaya, Cisco, Extreme Networks and Netgear, but also Apple, Google, Roku and Sonos and many other well-known providers.
A total of around 496 million network-capable end devices are currently expected to be affected. Through them it is possible to penetrate the networks of large and small companies. Armis even claims that hardly any company in the world is safe from attacks via DNS rebinding due to the high spread of vulnerable devices.
To protect against attacks like these, companies that want to extend their existing IT structures with IoT devices should work together with competent specialists. But malware protection programs, anti-virus scanners and common sense can also ward off numerous attacks. No Nigerian prince wants to give away his millions – and even the nice stranger who offers his help with router or PC configuration via email actually has other goals.